Insurance Fraud Cases
Manage client details, set custom billing rates, and automate email updates for efficient case handling. Enhance client satisfaction with streamlined communication and personalized service settings.
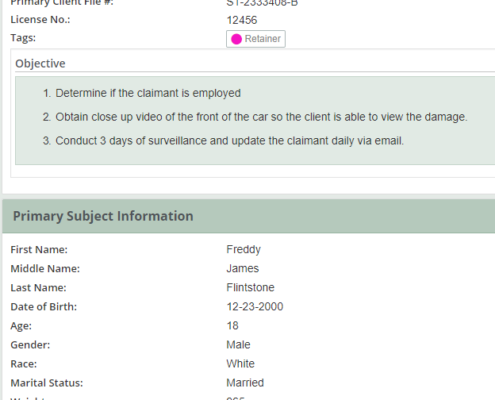
Meet and exceed the needs of insurance companies, insureds, TPA’s and defense attorneys.
CROSStrax has valuable features for insurance investigations. From AOE/COE, recorded statements, activity checks, alive and well, to surveillance, case management can be used to assist investigative efforts.
Note tasks and schedule investigators. Ensure date specific requirements are met.
Send updates with photos or video. The client has the option to view or download the file.
Don’t miss out on new business. CROSStrax exceeds requirements for vendor panels and RFP’s.
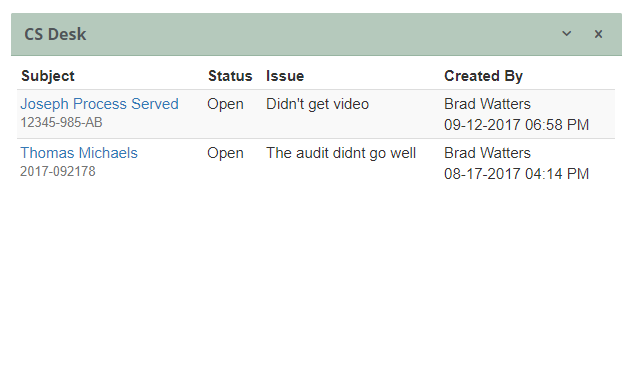
Stay aware and handle client issues
An investigator had car trouble on the way to a case.
A case was scheduled for the wrong day
Document these in the CS desk so the client and everyone involved in a case can be notified. Review the CS desk at certain intervals and address any recurring issues with your team.
Securely transmit and store work product
Unlike typical file storage solutions, CROSStrax is SOC 2 Type 2 certified — a prestigious and difficult-to-achieve distinction that ensures your investigative files are protected with the highest levels of security and encryption.
We all know losing a client is expensive. So is using multiple programs to handle the amount of video, photos and audio insurance investigations can produce. A well known file sending and backup service starts at $9.99 per month. When you start adding storage capacity to these services, they get expensive quickly.



