Locate & Background
Whether you’re tracking down a witness, subject, debtor, or missing person, CROSStrax gives you the tools to run efficient and fully documented locate investigations.
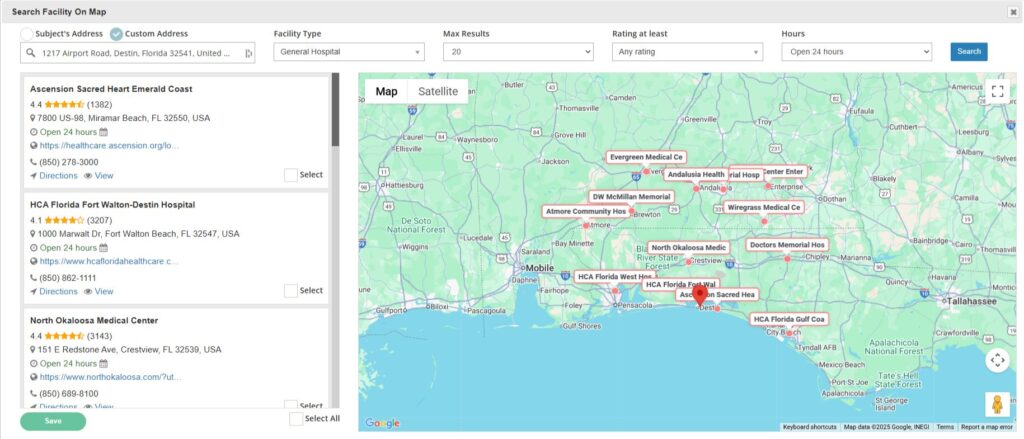
Why CROSStrax for Surveillance?
Many locates and background investigations are time sensitive. Whether an investigator is trying to find a missing person or hire a new employee, time is money. Run searches and upload the reports to the system. Create case notes with leads to follow up on or tips obtained during the day.
Features Built for Skip Tracing and Background Work
End-to-end solutions tailored for investigators, attorneys, and risk managers.

Centralized Data Entry
Store and organize personal identifiers, social profiles, addresses, and case notes in one place—eliminating duplication and confusion.

Structured Case Templates
Start each locate case with a consistent format. Log search results, sources, and leads using custom fields and investigator checklists.

Real-Time Updates
Assign tasks, upload findings, and communicate with your team or client—all with time-stamped transparency.

Document & Media Uploads
Attach photos, PDFs, and public record screenshots to support your findings and preserve evidence trail.

Progress Reporting
Generate easy-to-read summaries for clients or court, showing every step taken and every resource used.

Why Use CROSStrax for Locates?
Cold case investigations demand accuracy, organization, and the ability to track complex details over long periods. CROSStrax provides a digital infrastructure built specifically for that purpose—empowering investigative teams to manage historical cases with confidence and efficiency.
- Keep investigations organized and professional
- Speed up search efforts with reusable workflows
- Provide clean, detailed documentation for legal review
- Manage multiple locate cases at once without confusion
- Collaborate easily with team members or clients securely
Ready to Make Your Next Locate Easier?
Launch your first case in under a minute—no credit card required.



